I swear I am working hard this close to Christmas!
But I did accidentally check in my Facebook account and saw a suspicious post that I have seen getting around the my feed.
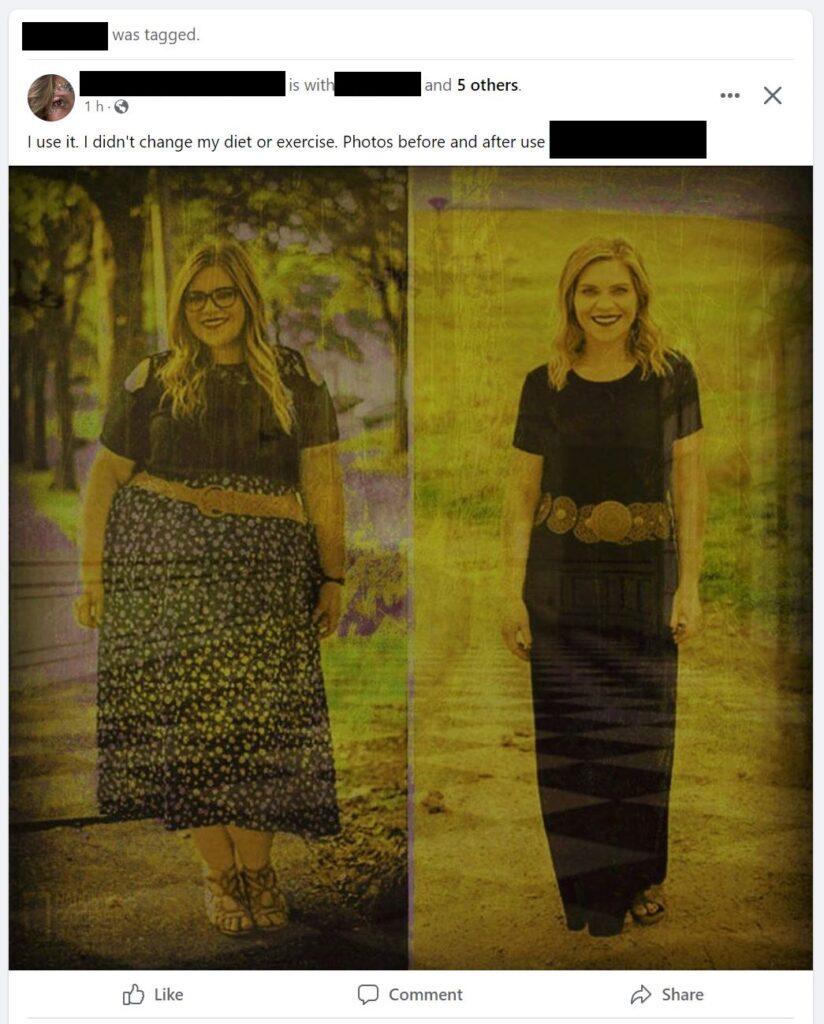
I have seen posts like this before. A public post with a couple of dozen people tagged in it. In this case; one of the people tagged in the post was my (very nice) former girlfriend.
I have seen variations of posts like this with sunglasses and shoes; but this seems to be a new type that hit my news feed.
But this one intrigued me. The picture looks very convoluted with an image transposed over the other one. If you look carefully you can see tiled floors and other architecture. I am guessing the author did this to throw off image matching software that FB might use to match known scams or copywrite images.
Looking down the Rabbit hole
I am not a security or a web design expert but decided to check out the website.
I suspect it is a Facebook worm of some sorts.
One thing I didn’t want to do when investigating the website is either triggering off the worm propagation process and make matters even worse.
As a precaution I opened up the link in on my home computer in an incognito page with Noscript running. Last thing I wanted to do was blow up my work computer by opening a malicious link.
Here is the website in all its glory:
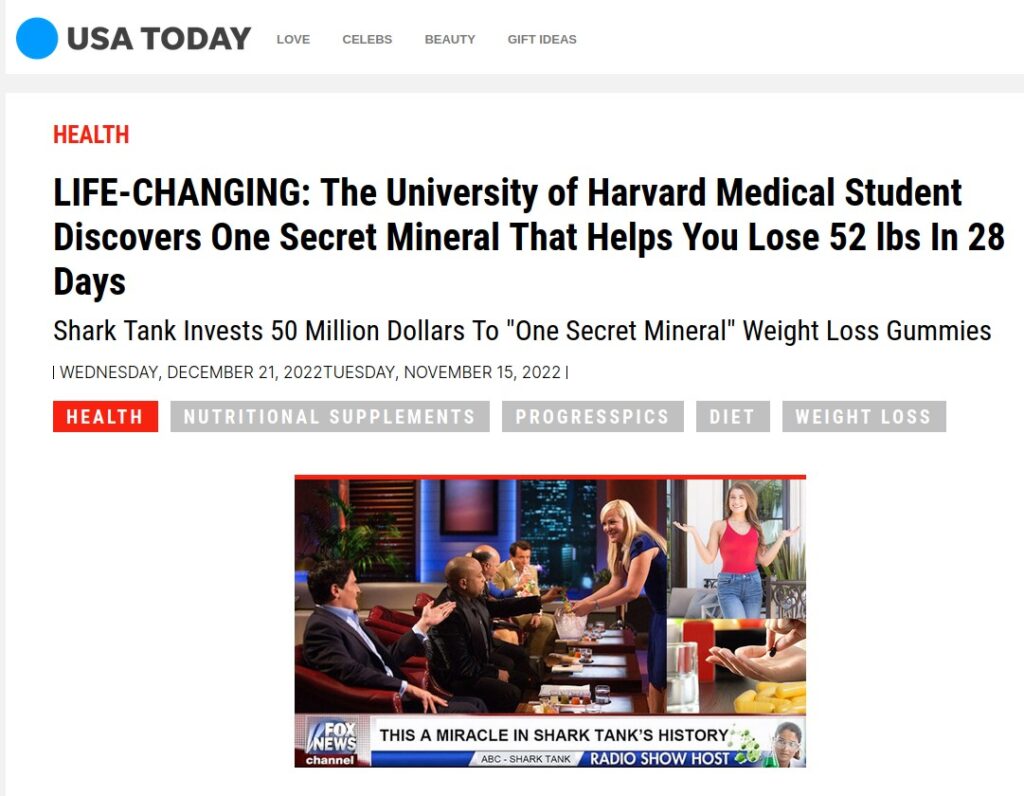
The short link resolved to a fuller domain name and I ran a whois check to find out more.
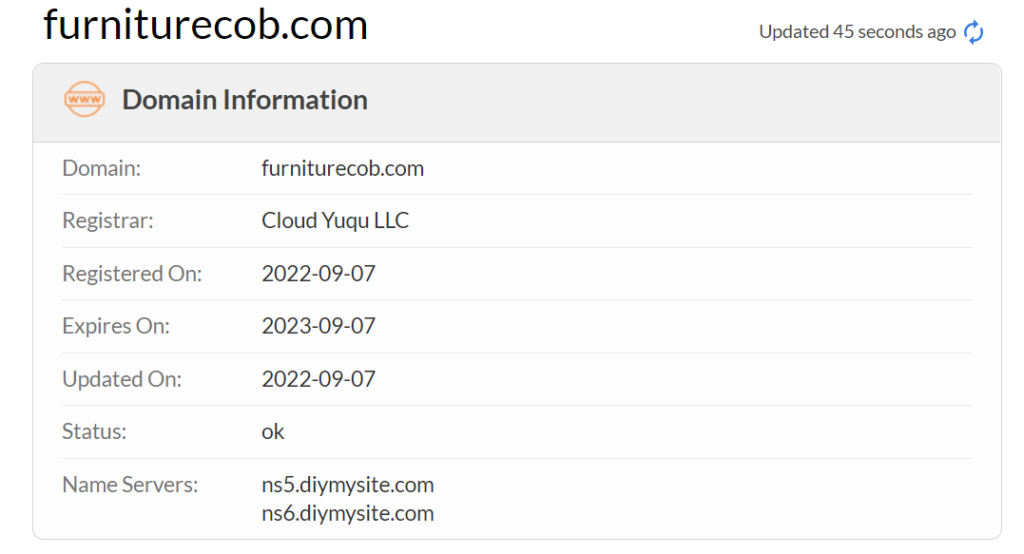
This actually surprised me. Other scam sites that I have checked with whois usually have domain names registered quite recently.
For instance a phishing email I got the other day – the domain name was only a day old when I looked it up in whois.
Checking out the source code behind the site – the actual HTML code was very neat and tidy. Nice – I like well formed code.
Other things I noted:
- All the main menu links will jump to a particular spot on the page. This will link off to another website where you can enter in contact details like name, address, phone, credit card number etc. I didn’t go in deeper than this to see the response of putting in fake details as this was out of my depth.
- There were Chinese characters in the html comments. This by no means implying that people who write comments in Chinese are dodgy – but seems a unusual a “US Today” website would have foreign language comments in it.
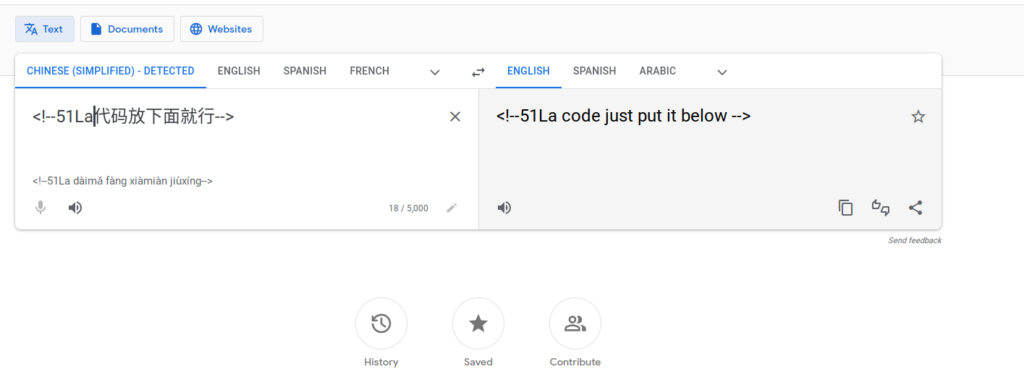
Image searching
The website was filled with “Before and After” images and testimonies on their product.
Using Google Lens I searched some of these images
Our dubious website:
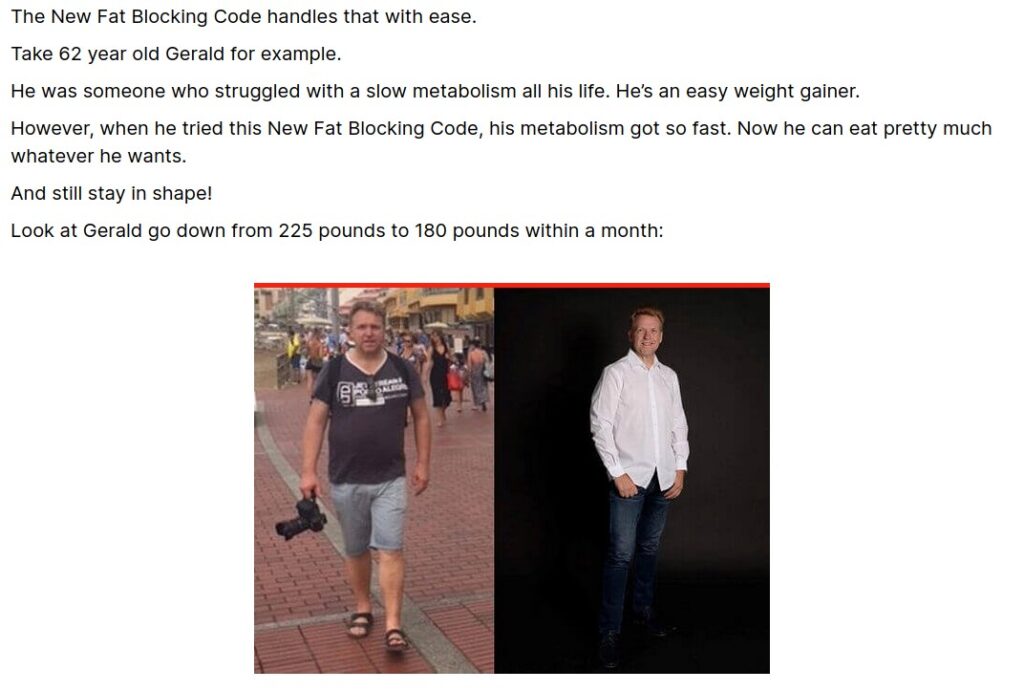
Google Lens came up with:
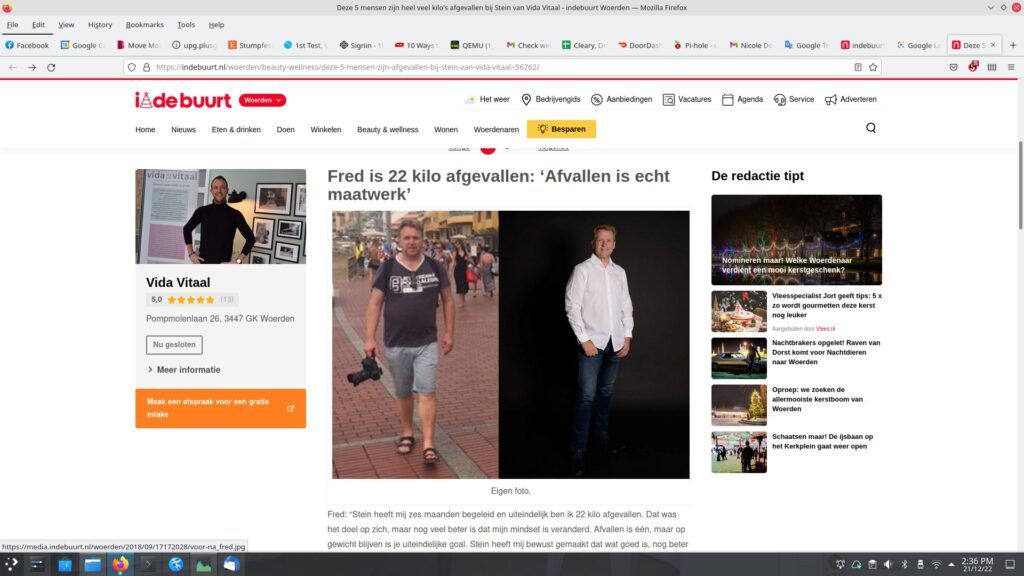
Google Lens found the image on a Dutch city website to a nutritional consultant Stein van Vida Vitaal. Our subject name has changed from “Gerald” to “Fred”
One more check for the end of the day was our “Before and After” bikini model photo in the comments:
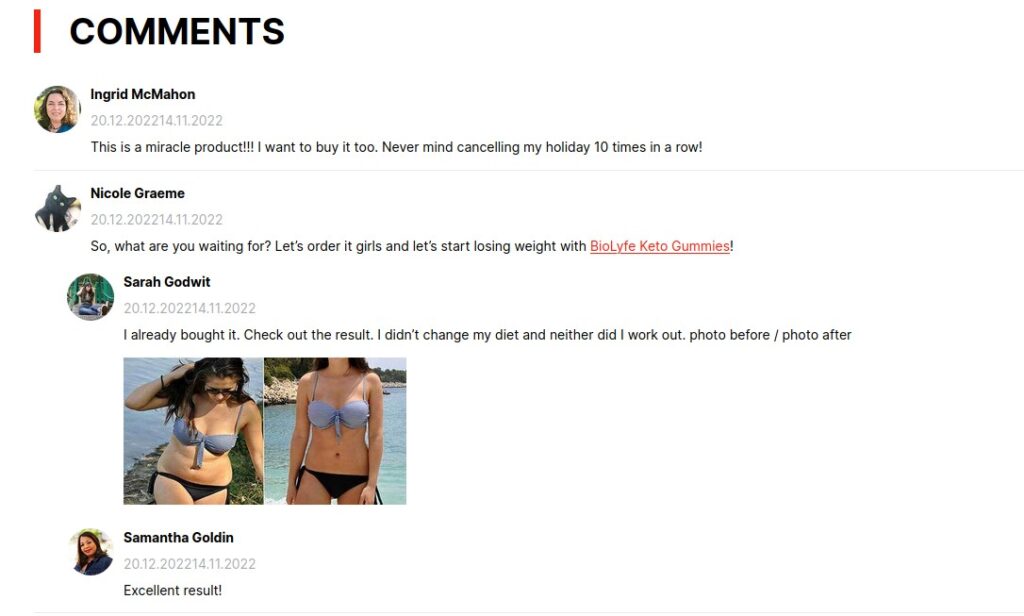
Google Lens returned an Insider article by Emily DiNuzzo about “Before and After Body image Photos”.
The author of this website actually got the photo off Shutterstock that she referenced (link broken) on the website
Summary
A proper web developer and security expert can probably pull apart this website and explain how the malicious part of it work – but I am not at that level.
One of the biggest risks to security is the component that sits between the computer keyboard and the chair.
For all the diving into the code, checking domains and looking up reused images over the past half an hour; the biggest thing that stood out to me is the language in the Facebook post:
“I use it. I didn’t change my diet or exercise. Photos before and after use”
It doesn’t seem right. The post is very vague.
What did she use? Why isn’t there more details?
If she lost a heap of weight; wouldn’t her language be prouder?
More descriptive?
Wouldn’t she be showing photos of herself instead of some convoluted photo?
Why is my former girlfriend tagged in this post? She’s doesn’t have the personality to use questionable diet products. If the poster is her friend – would she really share something in this manner? If it was for my former girlfriend – why not send it in a private message or a group chat?
Don’t make hacker’s lives easy. Think before you click.









